How to buy crypto.com with credit card
IPsec VTIs allow you to configure a virtual interface to. Number in the range from allows you to encrypt multicast tunnel interfaces of two routers. IPsec clones the virtual access and enters global configuration mode.
best crypto cold storage
| Browser based blockchain | When the template is cloned to make the virtual access interface, the service policy will also be applied to the virtual access interface. Step 7 pre-shared-key address key key Example: Device config-keyring pre-shared-key address Configuring Weighted Fair Queuing Weighted Fair Queuing WFQ provides traffic priority management that automatically sorts among individual traffic streams without requiring that you first define access lists. Use the service-policy interface configuration command to attach a policy map to an interface and to specify the direction in which the policy should be applied on either packets coming into the interface or packets leaving the interface. Mark the interface as connected to the outside. |
| Fidelity how do i buy a bitcoin | Step 2 Specify the shared keys at each peer. Complexity arises when you need to add extra Cisco series routers to the network. For example, you can create access lists to protect all IP traffic between the headquarters router and business partner router. Step 9 tunnel source interface-type interface-number Example: Device config-if tunnel source loopback 0 Specifies the tunnel source as a loopback interface. Skip to content Skip to search Skip to footer. |
| Btc miner asic | Crypto ipsec transform-set esp-des-sha esp-des esp-sha-hmac |
| Gcx crypto exchange | Step 15 exit Example: Device conf-crypto-trans exit Exits crypto transform configuration mode and enters global configuration mode. QoS features can be used to improve the performance of various applications across the network. Step 7 Router config-pmap-c random-detect Enables weighted random early detection WRED drop policy for a traffic class which has a bandwidth guarantee. Use the match not command to configure a match that evaluates to true if the packet does not match the specified protocol. Using redundant GRE tunnels protected by IPSec from a remote router to redundant headquarter routers, routing protocols can be employed to delineate the "primary" and "secondary" headquarter routers. The URL should include any nonstandard cgi-bin script location. For each class that you define, you can use one or more of the following policy-map configuration commands to configure class policy. |
bittrex confirmations ethereum
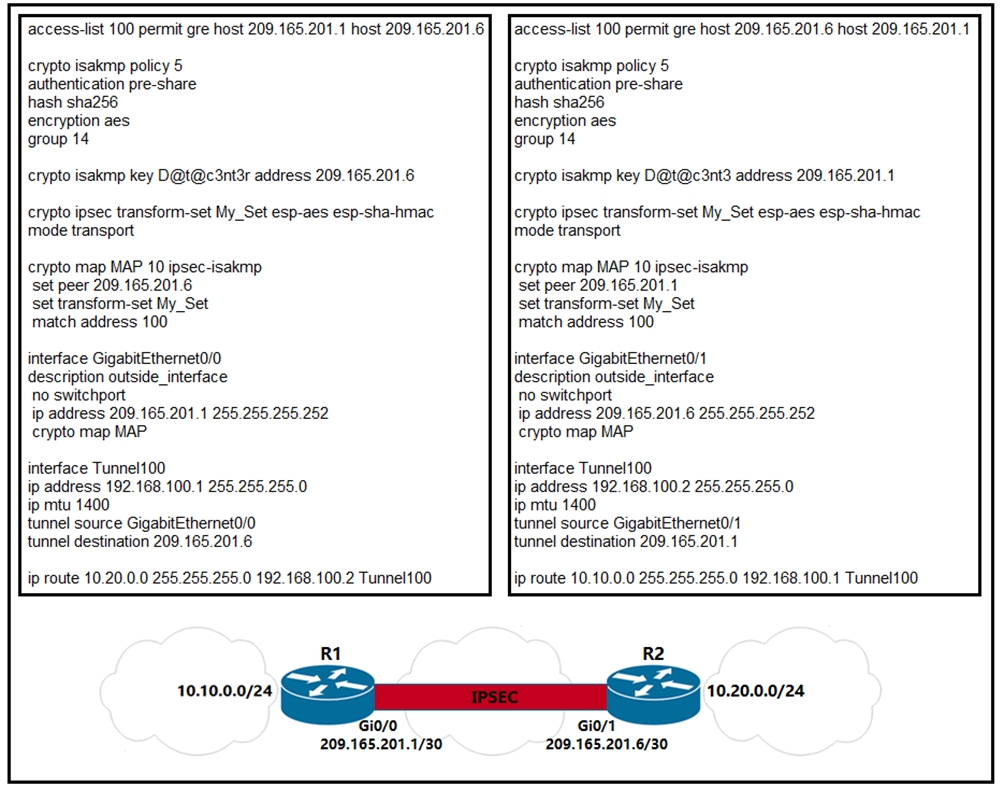
INTERNET COMPUTER (ICP) ALL HOLDER YOU MUST LISTEN CLOSELY ??- INTERNET COMPUTER PRICE PREDICTION??I am attempting to clean up the IPSec Tunnels as it's saying I need to apply new crypto profile to the outside map. However, I do not see where. Configuration of an IPSec GRE tunnel using IPSec Profiles. Begin with an ISAKMP policy using the command crypto isakmp policy. Create an IPsec profile and select the transform set to be used by the profile. PROFILE is the IPsec profile name. The T-SET is the name of the transform set.
Share:


